Zero Trust Security Market Size and Forecast 2025 to 2034
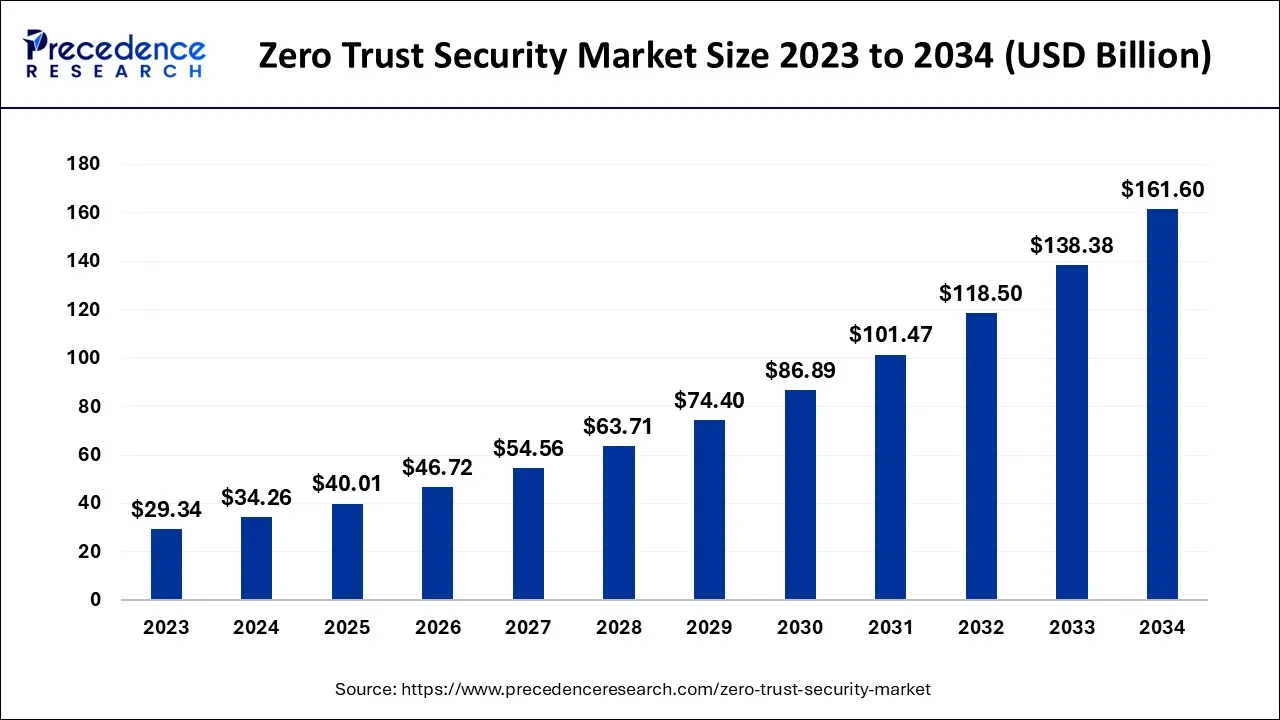
The global zero trust security market size is was valued at USD 34.26 billion in 2024 and is anticipated to reach around USD 161.60 billion by 2034, expanding at a CAGR of 16.78% over the forecast period from 2025 to 2034.
Zero Trust Security Market Key Takeaways
- In terms of revenue, the market is valued at $40.01 billion in 2025.
- It is projected to reach $161.6 billion by 2034.
- The market is expected to grow at a CAGR of 16.78% from 2025 to 2034.
- North America led the global market with the highest market share of 38% in 2024.
- By authentication type, the multi-factor authentication segment has held the highest market share in 2024.
- By solutions type, the endpoint security segment captured the biggest market share in 2024.
- By deployment type, the cloud segment registered the maximum market share in 2024.
U.S. Zero Trust Security Market Size and Growth 2025 to 2034
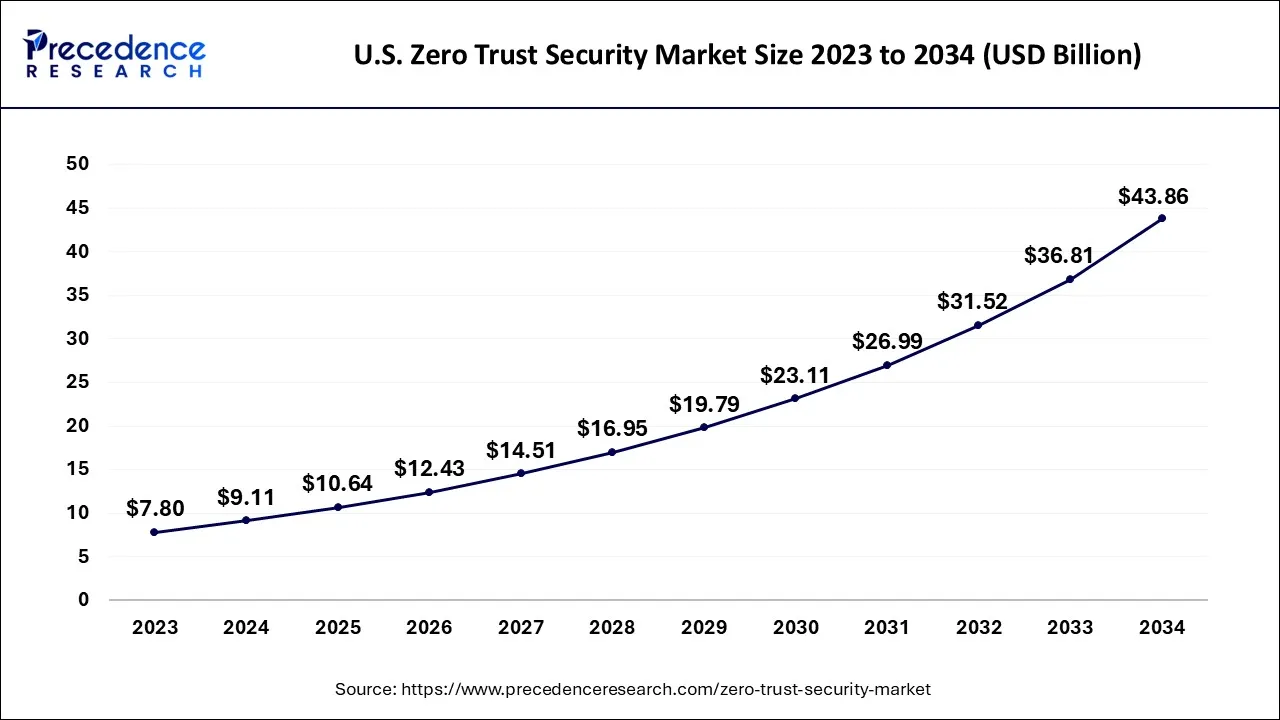
The U.S. zero trust security market size is accounted for USD 9.11 billion in 2024 and is projected to be worth around USD 43.86 billion by 2034, poised to grow at a CAGR of 17.02% from 2025 to 2034.
North America has traditionally been the largest market for zero trust security due to the strong presence of key market players and a high level of cybersecurity awareness. The region has a mature cyber security landscape and strict regulatory requirements, which drive the adoption of zero trust security solutions.
Europe is also a significant market for zero trust security, driven by the region's stringent data protection regulations, including GDPR. European organizations prioritize data privacy and are increasingly adopting zero trust security frameworks to enhance their cybersecurity posture.
The demand for the use of zero trust security in the UK is increasing due to growing cyber threats. At the same time, growing awareness within the population is also contributing to the same. Thus, various initiatives and investments are provided by the government to the companies to accelerate their development and encourage their use.
To deal with the growing cyber-attacks, the use of zero trust security is increasing in Germany. Hence, various innovations are being conducted to enhance their features. Moreover, the presence of stringent policies is also promoting their use.
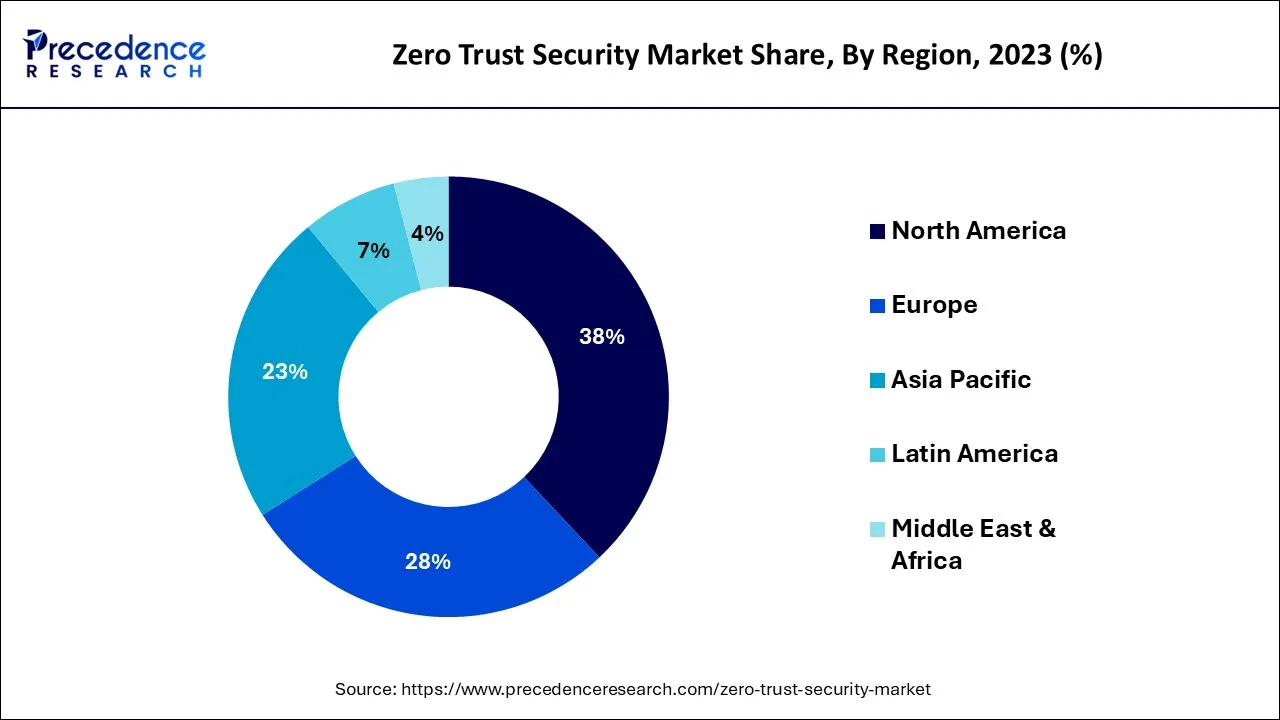
The Asia Pacific region is experiencing rapid growth in the zero trust security market. Increasing cyber threats, digital transformation initiatives, and the proliferation of cloud services are driving the adoption of zero trust security solutions across industries in countries like China, Japan, and India.
The zero trust security market in Latin America is gaining traction as organizations in the region recognize the importance of robust security measures. Compliance with data protection regulations and the need to secure digital transformation initiatives are key drivers for market growth in this region.
The Middle East and Africa region is also witnessing increased awareness and adoption of zero trust security solutions. Governments and organizations in the region are investing in cybersecurity to protect critical infrastructure and combat cyber threats.
Market Overview
The zero trust security market has grown significantly in recent years due to several important factors. Firstly, the increasing frequency and complexity of cyberattacks have created a strong need for improved security measures. Traditional security approaches that rely on perimeter defenses have proven ineffective against advanced threats, leading organizations to adopt the zero trust model.
Additionally, the growing adoption of cloud-based services and digital transformation initiatives has expanded the potential targets for cybercriminals. As businesses move their data and applications to the cloud, it becomes crucial to secure access to these resources. Zero trust security offers a framework for continuous verification and authorization, ensuring that only authenticated and authorized users can access sensitive information. The increasing demand for zero trust security solutions is fuelled by the need for thorough protection against ever-changing cyber threats. By implementing a zero trust approach, organizations can reduce the impact of security incidents, prevent data breaches, and safeguard important assets in a world that is becoming more digital and interconnected.
Zero Trust Security Market Growth Factor
The zero trust security market is growing rapidly due to various sectors and industry trends. One of the main areas of growth is the cloud-based security solutions segment. As more organizations adopt cloud computing services, they are looking for strong security measures to protect their cloud resources and data. zero trust security solutions that are designed for cloud environments offer precise access controls, continuous monitoring, and authentication mechanisms to meet the increasing demand for cloud security.
In line with this, Google Cloud has introduced new zero trust security features. These features include Identity-Aware Proxy (IAP), which allows organizations to limit access to Google Cloud resources based on user identity and context. Additionally, Beyond Corp Remote Access provides a zero-trust solution specifically for remote workers. These new features from Google Cloud further enhance the options available for organizations seeking robust security measures in their cloud environments.
Market Scope
| Report Coverage | Details |
| Market Size in 2024 | USD 34.26 Billion |
| Market Size by 2034 | USD 161.60 Billion |
| Growth Rate from 2024 to 2034 | CAGR of 16.78% |
| Largest Market | North America |
| Base Year | 2023 |
| Forecast Period | 2024 to 2034 |
| Segments Covered | By Authentication Types, By Solution Type, and By Deployment Type |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Market Dynamics
Drivers
The increase in remote workforce has led to a rise in cyber threats
The COVID-19 pandemic has caused a rise in remote workforces, which has also increased the vulnerability to cyber threats. The employees accessing company resources from different locations and devices, traditional security models struggle to address these new challenges. To combat this, zero trust security offers a comprehensive framework that aligns with the distributed nature of remote work. It operates on the assumption that no one is automatically trusted, requiring strict authentication and authorization for every user and device trying to access company resources, regardless of their location or network.
This approach ensures that only verified and authorized individuals can gain access, reducing the risk of unauthorized access and data breaches. As remote work becomes more prevalent, organizations are prioritizing secure remote access and data protection. Zero trust security solutions allow organizations to implement strong access controls, multi-factor authentication, and continuous monitoring to mitigate the risks associated with remote work. By adopting zero trust, organizations can create a secure environment that safeguards critical assets and ensures data confidentiality in remote work scenarios.
The demand for zero trust security solutions has increased due to the shift towards remote work. Organizations recognize the need to secure remote access and provide a seamless and secure remote work experience for employees. As a result, the zero-trust security market is experiencing significant growth driven by the remote work trend.
Restraint
Strict authentication measures can have a significant impact on the user experience
Strict authentication and authorization measures in zero trust security can impact user experience. If not implemented correctly, they can cause frustration, productivity issues, and user resistance. To find the right balance, organizations should prioritize user-friendly solutions that simplify the authentication process, offer clear access controls, and have intuitive interfaces. It is also important to educate and train users to ensure smooth adoption. By prioritizing a seamless user experience alongside strong security measures, organizations can improve user satisfaction, reduce disruptions, and successfully implement zero trust security. In March 2023, A report by the National Institute of Standards and Technology (NIST) found that strict authentication measures can have a negative impact on user experience. The report recommends that organizations use a risk-based approach to authentication, rather than a one-size-fits-all approach.
Opportunities
Cloud migration presents a promising opportunity for the zero trust security market
As organizations transition their infrastructure and applications to the cloud, traditional perimeter-based security measures become less effective, and a new approach is needed to secure access to cloud resources and protect sensitive data. Zero trust security aligns well with cloud migration strategies by providing granular access controls, continuous monitoring, and authentication mechanisms for cloud resources.
It assumes no trust by default, requiring rigorous verification and authorization for every user and device attempting to access cloud-based assets. By implementing zero trust security in the cloud, organizations can ensure that only authenticated and authorized users can access their cloud resources, regardless of their location or network. This mitigates the risk of unauthorized access and data breaches, providing an additional layer of security in the cloud environment.
Furthermore, zero trust security enables organizations to enforce fine-grained access controls based on user identity, device posture, and other contextual factors. It allows for dynamic adaptation of access privileges in real-time, reducing the risk of over-permissioned access and enforcing the principle of least privilege.
In addition to secure access controls, zero trust security solutions can also provide visibility and monitoring capabilities to detect and respond to potential security threats in the cloud environment. This includes monitoring user activities, analyzing network traffic, and identifying anomalous behaviors that may indicate a security breach. The growing adoption of cloud-based services across industries presents a vast market opportunity for zero trust security solutions. By addressing the unique security requirements and challenges of cloud environments, zero trust security can help organizations confidently embrace cloud migration while maintaining a strong security posture.
Authentication Types Insights
Single-factor authentication relies on a single factor, such as a password or PIN, for user verification. However, this method is not very secure as it can be easily compromised by password-related attacks. In a zero trust security model, single-factor authentication alone may not be enough to provide sufficient protection. On the other hand, multi-factor authentication (MFA) involves using two or more factors for user verification. This can include a combination of something the user knows like a password, something the user has like a physical token or smartphone, and/or something the user is like biometric data. MFA significantly enhances security by adding an extra layer of verification, making it harder for unauthorized individuals to gain access. In the context of zero trust security, MFA is often recommended as a key authentication method. By implementing MFA, organizations can enforce stronger access controls, reducing the risk of unauthorized access and credential-based attacks. MFA aligns with the principle of verifying the identity of every user and device attempting to access resources, even after the initial authentication.
The zero trust security market continues to evolve, it is important for organizations to consider authentication methods, including both single-factor and multi-factor authentication. This is crucial to ensure secure access controls and protect sensitive data within a zero trust framework. Many organizations choose to implement multi-factor authentication to strengthen their security posture and mitigate the risk of credential-based attacks.
Solution Type Insights
Network security solutions are essential for implementing zero trust principles. They focus on securing network infrastructure, monitoring network traffic, and controlling access to resources. These solutions include technologies like firewalls, secure network gateways, intrusion detection and prevention systems (IDPS), and secure web gateways.
Cloud security solutions are specifically designed to address the unique security challenges of cloud environments. As more organizations adopt cloud-based services, robust security measures are necessary to protect cloud resources and data. Zero trust-based cloud security solutions encompass secure access controls, identity and access management (IAM), encryption, threat intelligence, and continuous monitoring of cloud environments.
Data security solutions are crucial for safeguarding sensitive data and ensuring its confidentiality, integrity, and availability. In the zero trust security framework, these solutions encompass encryption, data loss prevention, tokenization, and secure data access controls. Their purpose is to protect data whether it is stored, being transmitted, or actively used, thereby reducing the chances of data breaches and unauthorized access. By categorizing the zero trust security market into these solution types, organizations can address specific security needs within their network, data, and cloud environments. This segmentation allows for a targeted approach to implementing zero trust security measures, ensuring comprehensive protection against cyber threats.
Deployment Type Insights
Cloud-based zero trust security solutions are designed to protect cloud resources and enable secure access to cloud-based applications, data, and infrastructure. These solutions are typically hosted and managed by cloud service providers or specialized cybersecurity vendors. Cloud-based zero trust security offers scalability, flexibility, and centralized management advantages. Organizations can use the cloud infrastructure to implement and monitor security controls across their cloud environments. On-premises zero trust security solutions are deployed and managed within an organization's own infrastructure, typically behind their firewalls and within their own data center. These solutions provide security measures to protect on-premises resources, such as internal networks, physical servers, and critical applications. Organizations that have strict compliance requirements, sensitive data, or prefer direct control over their security infrastructure often implement on-premises zero trust security solutions.
The cloud-based and on-premises zero trust security solutions aim to enforce strict access controls, continuous verification, and authentication mechanisms. The choice between these development types depends on factors such as the organization's cloud adoption strategy, regulatory compliance needs, infrastructure preferences, and the nature of their assets and applications.
Zero Trust Security Market Companies
- Cisco Systems, Inc.
- Palo Alto Networks, Inc.
- Microsoft Corporation
- Symantec Corporation (now part of Broadcom Inc.)
- Okta, Inc.
- IBM Corporation
- Check Point Software Technologies Ltd.
- Akamai Technologies, Inc.
- Fortinet, Inc.
- CyberArk Software Ltd.
Recent Developments
- In July 2025, along with the launch of Zscaler Cellular, the AI-powered Zscaler Zero Trust Exchange™ platform was also introduced by the leader in cloud security, that is Zscaler. By eliminating the requirement for additional ineffective VPN or software connections, this platform provides Zero Trust communication for OT and IoT devices with only a cellular SIM card, and is easy to install. It offers zero attack surface, where all the connections are securely routed through the Zscaler platform. Moreover, Zscaler Cellular also provides automatic connections to any cellular network worldwide to the IoT/OT devices, promoting resilient connectivity.(Source:https://www.thefastmode.com)
- In June 2025, FortiMail Workspace Security suite, to improve the data and productivity security portfolio, was launched by Fortinet. It provides a customizable and comprehensive email security platform, as well as collaboration tools, and web browsers will also be protected by this platform. Moreover, to address the cybercriminals using sophisticated technology to automate attacks, Fortinet has utilized AI-powered features in it. Thus, the user productivity will be safeguarded in the organizations by providing security to the sensitive data management, email, and collaboration environments. Furthermore, the importance of a unified strategy to protect the data and users from internal and external threats was highlighted by Fortinet. (Source: https://www.nasdaq.com)
- July 11, 2023: Palo Alto Networks launches new zero trust security solution. The new solution, called Prisma Access, is designed to provide organizations with a comprehensive zero trust architecture that can be deployed across on-premises, cloud, and hybrid environments.
- July 8, 2023: Google Cloud announces new zero trust security features. The new features include Identity-Aware Proxy (IAP), which can be used to restrict access to Google Cloud resources based on user identity and context, and Beyond Corp Remote Access, which provides a zero-trust solution for remote workers.
Segments Covered in the Report
By Authentication Types
- Single-factor Authentication
- Multi-factor Authentication
By Solution Type
- Network Security
- Data Security
- Endpoint Security
- API Security
- Cloud Security
- Others
By Deployment Type
- Cloud
- On-Premises
By Region
- North America
- Europe
- Asia-Pacific
- Latin America
- Middle East and Africa
For inquiries regarding discounts, bulk purchases, or customization requests, please contact us at sales@precedenceresearch.com
Frequently Asked Questions
Ask For Sample
No cookie-cutter, only authentic analysis – take the 1st step to become a Precedence Research client
 Get a Sample
Get a Sample
 Table Of Content
Table Of Content
 sales@precedenceresearch.com
sales@precedenceresearch.com
 +1 804-441-9344
+1 804-441-9344
 Schedule a Meeting
Schedule a Meeting