Quantum computing could soon break todays encryption, putting business data at risk. Companies must act now by upgrading security, adopting post-quantum cryptography, training teams, and following new standards to stay protected in the coming digital future.
Key Takeaways
- The approaching post-quantum era is demanding immediate business attention.
- Businesses are very likely to face quantum cryptographic attacks in the next five years.
- Top companies are creating a clear path to overcome quantum cybersecurity attacks by predicting risk, planning, and implementing strong actions.
- Companies are focusing on prioritizing the development of modernized technologies and solutions to fight quantum cybersecurity attacks in the future.
- The establishment of a quantum-ready ecosystem is at its verge.
- Industries need to invest heavily in a quantum-ready ecosystem to secure their business in the upcoming years.
- Governments across the world are creating a support environment for vendors to develop quantum-resisted system.
What is Quantum Threat and how can it Effect Your Business?
Cryptographic mechanics are the backbone of modern digital infrastructure, businesses, and government institutions, and enable citizens to operate with confidence and trust in online environments. Post-quantum cybersecurity is a major threat to businesses, as quantum computers can break current encryption methods. Quantum computing has the potential to break majorly used public key algorithms.
Quantum computing is projected to break over 50% highly used today’s cryptographic algorithms like RSA-2048 by 2035. The possibilities are high as the “Quantum Utility” era is on the way to wrap global organizations. The need for a huge computational power supply is emerging, making it difficult for businesses to prevent them from cyberthreats.
Rapid growth of quantum computing is at verge to create high-risk for data and systems, making it threatening to different businesses, especially finance, health, defense, government, and energy. Businesses are likely to face migration challenges, as the PQC transition will be difficult. The need for significant updates and innovations for the legal system, third-party integration, and APIs is becoming crucial.
Major Quantum Threat Warning by Top Tech Companies:
- In January 2026, at the World Economic Forum, the CEO of IonQ warned that “Q Day” would become a breakable of widely used public key cryptography in the next three years.
- Brain & Company also warned about a quantum threat to be imminent and not hypothetical; the concern was raised in January 2026.
- Also in December 2025, Google revealed that today's quantum computing is at a significant stage compared to artificial intelligence five years ago, and is very likely to become more rapid and disruptive.
- Approximately 70% technological companies are predicting a rise of quantum threat in the next five years, and around one-third within three. However, the global quantum industry is witnessing no actions from the majority of organizations, as a given excuse for other organizations to take the lead.
What is the Cybersecurity Services Market Size?
The global cybersecurity services market size is accounted at USD 177.27 billion in 2025 and predicted to increase from USD 188.66 billion in 2026 to approximately USD 310.35 billion by 2034, expanding at a CAGR of 6.42% from 2025 to 2034. The growth of the cybersecurity services market is driven by rising cyber threats, regulatory compliance demands, and increased digital transformation across industries.
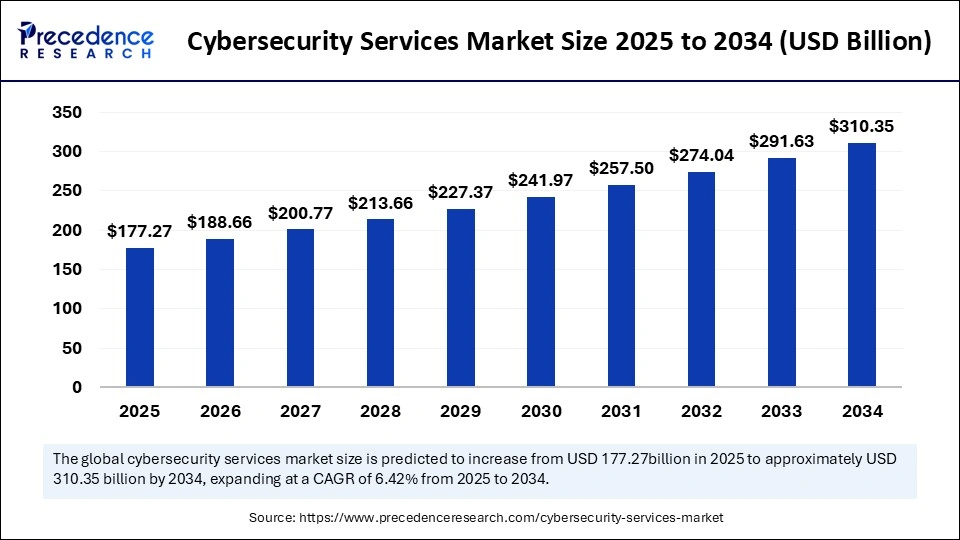
Cybersecurity Services Market Key Takeaways
- North America dominated the global market with the largest market share of 40% in 2024.
- Asia Pacific is expected to expand at the fastest CAGR during the forecast period.
- By service, the professional services segment captured the biggest market share in 2024.
Mostly Predicted Quantum Attack on Vendors
| Businesses | Industries | Possible Quantum Attacks |
| Financial | Retail, Manufacturing, Information | Criminals, Corporate Spies, and Insiders |
| Espionage | Government, Automotive, Building & Construction | State-sponsored, Corporate spies, and Insiders |
| Political | Information and Utilities | State-sponsored, Hacktivists, and terrorists |
In 202, the IBM IBV (IBM Institute for Business Value) engineered its Quantum Readiness Index (QRI) for identification of organizations to drop on the readiness spectrum. This definition defines a quantum-ready organization to take action and propel on its quantum journey.
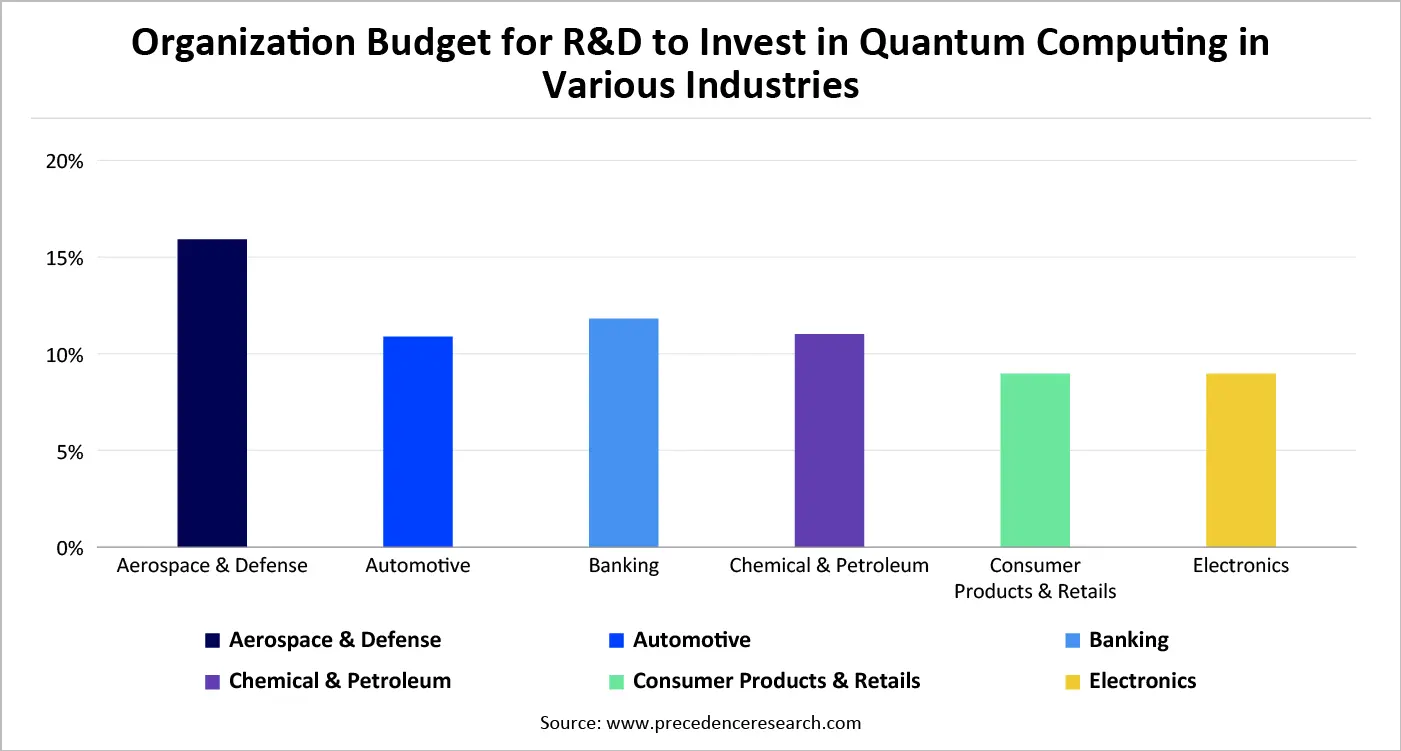
As per the C-suite executives' in-depth survey, the data revealed that 750 organizations from 28 countries and 14 industries reveal both progress and persistent gaps in 2025. According to the survey, in 2025, quantum computing has gain 11% of research and development budgets on average of above 7% compared to 2023.
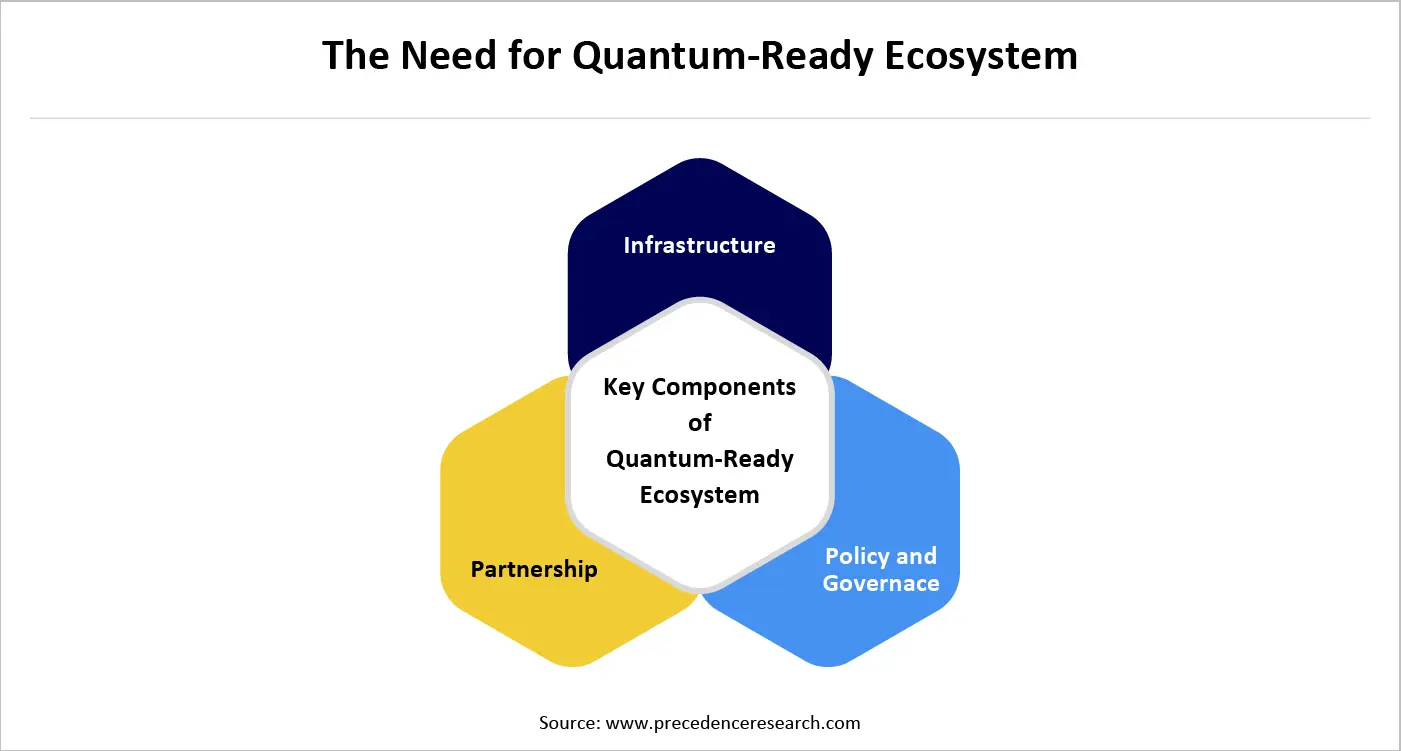
To support businesses in overcoming quantum cybersecurity attacks, the need for a quantum-ready ecosystem is emerging. Businesses are rapidly required to gear up for the quantum cybersecurity threats, and a quantum-ready ecosystem is exactly the catalyst to future-proof. To establish the quantum-ready ecosystem, there are a few key trades that need to be worked on, including crypto-agility, quantum-safe cryptography, risk assessment, and quantum key distribution (QKD).
What Key Aspects are Required for the Quantum-Ready Ecosystem?
- Talent and Skills Gap: To establish a quantum-ready ecosystem, the need for upskilling teams and fostering interdisciplinary expertise is emerging. These talents and skills can work as a project to transition from research to production.
- Cybersecurity Defense: The quantum-ready ecosystem is highly demands for cybersecurity defense. The only quote of “Harvest Now, Decrypt Later” is to meet with current encryption standards, which brings a vulnerable future to quantum attacks. This step focuses on the adoption of post-quantum cryptography (PQC) now to secure the future of data.
- Time-to-Value Acceleration through Hybrid Approaches: Classical computing is not being immediately replaced by quantum, but is being improved by it. The emerging integration of quantum, AI, and classical HPC is set to become a significant player in resolving difficult issues with great speed.
- Edge Competition and Innovation: To achieve a quantum-ready ecosystem, vendors are required to bring expertise, developed internal capabilities, and solutions to detect use cases in optimization and simulation, so these businesses can take a early-move advantages step forward.
What Preparation Strategies can Business Pull-off?
Businesses can prevent themselves by working on strategic preparations, including;
- By partnering with other industry players and staying updated on PQC standards.
- Enabling hybrid cryptography approaches for fast and risk-free transactions.
- Prioritizing high-risk systems and inventory cryptographic assets.
Companies are working hard to maintain AI workflows within consumers' jurisdictional control, to reduce the security risk, such as public quantum clouds and centralized clouds. For instance, SuperO Quantum Computing Inc. planned to unveil its Sovereign Hybrid-Cloud Infrastructure on February 11, 2026. The company is expected to shift its enterprise emphasis on localization, high-security compute nodes for energy, defense, health, and financial sectors.
How to Secure the Post-Quantum Future?
| Best Practice Focus | Way to Approach |
| Development of Crypto-Agility | IT architecture needs to be modernized enough so that it can allow rapid and seamless replacement of cryptographic algorithms, while seamlessly running business processes. |
| Cryptographic Assets Audit and Inventory | Identification of all applications, data, and system which uses public-key cryptography and classify them by longevity and strong emphasis on informative insights. |
| Current Security Boost | To strengthen the current security system, the upgradation of symmetric encryption, like AES-256, is essential. |
| Transition to PQC Standards | Post-quantum cryptography algorithms, which have been finalized by NIST, should come into force. |
| Governance Establishment | Designing a quantum risk task force for transitioning technologies and training staff is crucial. |
Most Recent Industrial Investments for Post-Quantum Cybersecurity Research
- On February 9, 2026, Leclercq American Capital LLC invested in SandboxAO, a convergene pionnered company of artificial intelligence and quantum technologies. These investments have enabled confidence in platforms to tackle critical challenges in cybersecurity, innovate simulation, and next-generation sensing. The B2B software solutions developed by SandboxAO helps large-scal organization to secure their infrastructure against quantum threats, which have a high possibility to occur in the future.
- On the same day, February 9, 2026, Reliance Global Group, Inc. signed an agreement with Enquantum Ltd, which is a post-quantum cryptography technology company, address a significantly growing trend of global cybersecurity standards. The agreement follows Reliance's previously announced term sheet and is planned to close within 30 days.
What Government and Regulatory Bodies are Bringing on Table to Support Vendors?
Governments worldwide and regulatory frameworks are expanding their reach to support business through various mechanisms are legal policies, to make it easier for nations to depend on cryptography, ensuring secure communications, safe financial transactions, trusted digital identities, and protection of sensitive data and strategic information.
European and Asian countries are at the top where government is particularly established itself to a global leaders in digital technologies, including transactions, with the support of the largest and fastest-growing Internet user bases. To protect digital infrastructure and information, governance and policies are walking hand-in-hand across the globe.
Major Government Initiatives to Counter Post-Quantum Cybersecurity Threats:
European Government Acts to Support Vendors
- In European countries, the EU’s Digital Operational Resilience Act (DORA) and the updated Network and Information Security Directive (NIS2) have been launched to strengthen guidelines across encryption and securing key management crucial for complex sectors like energy, healthcare, and finance.
- Various cybersecurity agencies in Europe, including Germany's BSI (Bundesamt fur Sicherheit in der Informationstechnik), France’s ANSSI (Agence Nationale de la Sécurité des Systèmes d’Information), and the EU’s Agency for Cybersecurity (ENISA), are working on upgrading cryptographic guidelines.
- The National Cyber Security Center (NCSC) has been set up for a complex infrastructure for transitioning to PQC between now and 2031. The act not only inspiring business o adopt novel cryptographic tools but mandates migration timelines.
Asian Government Initiatives to Prevent Quantum Cryptography Attacks:
- A public-private group in Japan, Cyber Research Consortium, has developed and standardized PQC technologies.
- A task for creating a “Quantum Safe Ecosystem” has been formed by the Department of Science and Technology (DST), with the Indian National Quantum Mission Task Force backing a support reach. This creation force involves sub-groups to test or certify products and establish migration timelines for business.
- Also, with China’s Institute of Commercial Cryptography Standards (ICCS) initiation in development and standardizing post-quantum cryptography (PQC) algorithms, which are diverging from U.S.-led (NIST) efforts, is likely to establish a sustainable ecosystem in preventing quantum cybersecurity threats in the future.
USA Government Essential Action on Potential Post-Quantum Cybersecurity Attacks:
- In August 2024, the National Institute of Standards and Technology (NIST) finalized and published its post-quantum cryptography standardization, was finalized and published FIPS 203 (ML-KEM0, FIPS 204 (ML-DSA), and FIPS 205(SLH-DSA). The standardization offers the official standards for businesses to develop quantum-resistant solutions across the U.S.
- The Executive Orders for Action were proposed in 2026 to accelerate the adoption of quantum technologies and emphasize secure supply chains for these technologies.
- A four-pillar framework, which is risk assessment, planning, engagement, and implementation, has been established by the Cybersecurity and Infrastructure Security Agency (CISA). This initiative guides critical infrastructure businesses to transition to their quantum-safe system.
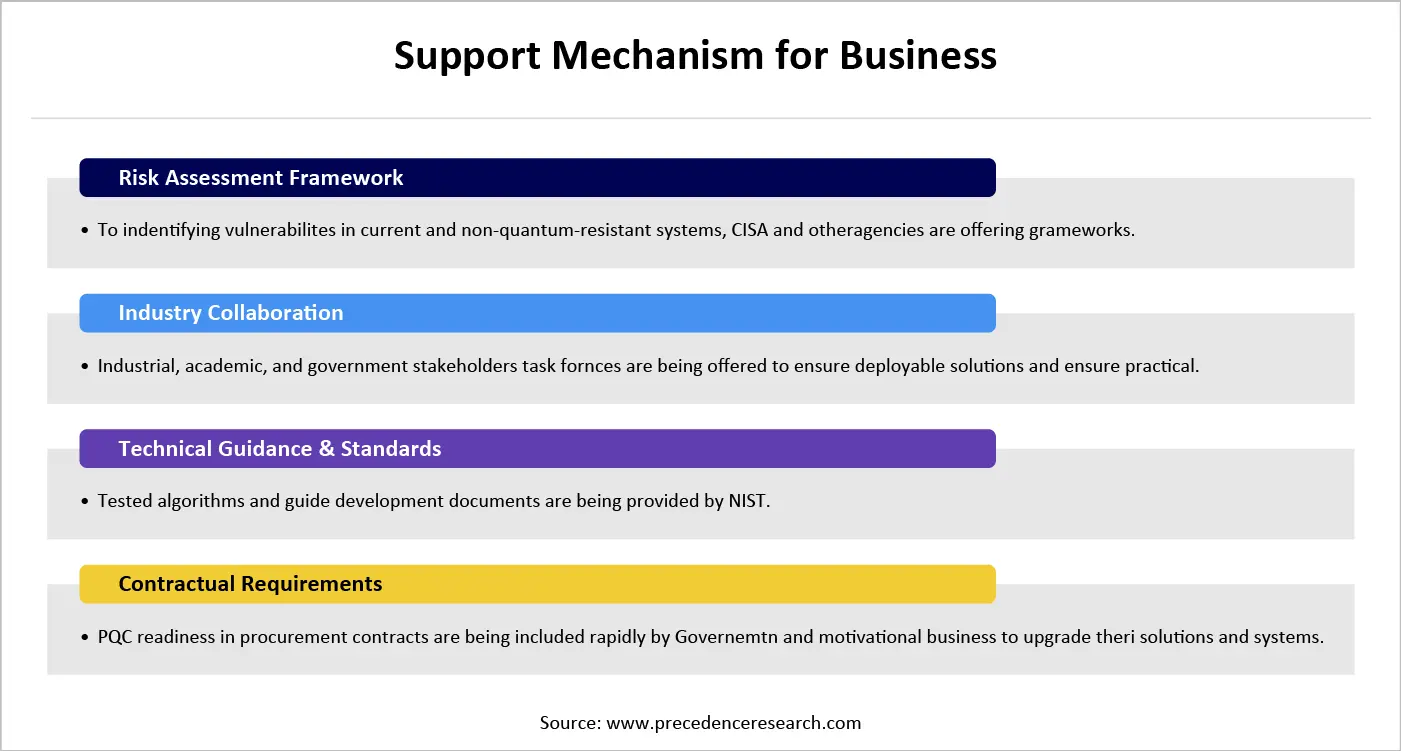
Last Step Action Plan to Prepare Business Overcome Post-Quantum Cybersecurity Threats:
Businesses are required to set an action plan as a full and final strategy to overcome quantum cryptography attacks, which includes an assessment of cryptographic assets and prioritizing high-risk systems now. Also, the development of a pilot and test quantum-safe solution will come in handy in urgent matters. Fortunately, this development is going to take time and a huge investment, but the emergency is emerging. Monitoring regulatory changes and threats can also help to established an secure environment. And last but not least, organizations can migrate to quantum-safe cryptography gradually.
Conclusion:
The risk of encryption is becoming huge with advancements in quantum computing technologies, likely to bring serious threats to various business infrastructures, such as the financial system, healthcare, sensitive data, and the nation. As the post-quantum era is cutting distance, businesses are sensing the need to pay attention and take action to prevent future damage. The more delay in preparation, more risk for the organization to face quantum cybersecurity attacks. The future is likely to become secure from post-quantum cybersecurity threats with strong industry investments in quantum-resistant technologies, hybrid security models, and government support.
The business demands urgency for structured planning, which can be fulfilled by an established quantum-ready ecosystem and collaborative approaches between technology providers, organizations, and policymakers. To secure a digital future in a post-quantum world, businesses should prepare today.
About the Authors

Aditi Shivarkar
Aditi, Vice President at Precedence Research, brings over 15 years of expertise at the intersection of technology, innovation, and strategic market intelligence. A visionary leader, she excels in transforming complex data into actionable insights that empower businesses to thrive in dynamic markets. Her leadership combines analytical precision with forward-thinking strategy, driving measurable growth, competitive advantage, and lasting impact across industries.

Aman Singh
Aman Singh with over 13 years of progressive expertise at the intersection of technology, innovation, and strategic market intelligence, Aman Singh stands as a leading authority in global research and consulting. Renowned for his ability to decode complex technological transformations, he provides forward-looking insights that drive strategic decision-making. At Precedence Research, Aman leads a global team of analysts, fostering a culture of research excellence, analytical precision, and visionary thinking.

Piyush Pawar
Piyush Pawar brings over a decade of experience as Senior Manager, Sales & Business Growth, acting as the essential liaison between clients and our research authors. He translates sophisticated insights into practical strategies, ensuring client objectives are met with precision. Piyush’s expertise in market dynamics, relationship management, and strategic execution enables organizations to leverage intelligence effectively, achieving operational excellence, innovation, and sustained growth.





 Request Consultation
Request Consultation

