Cybersecurity Mesh Market Will Grow at CAGR of 11% By 2033
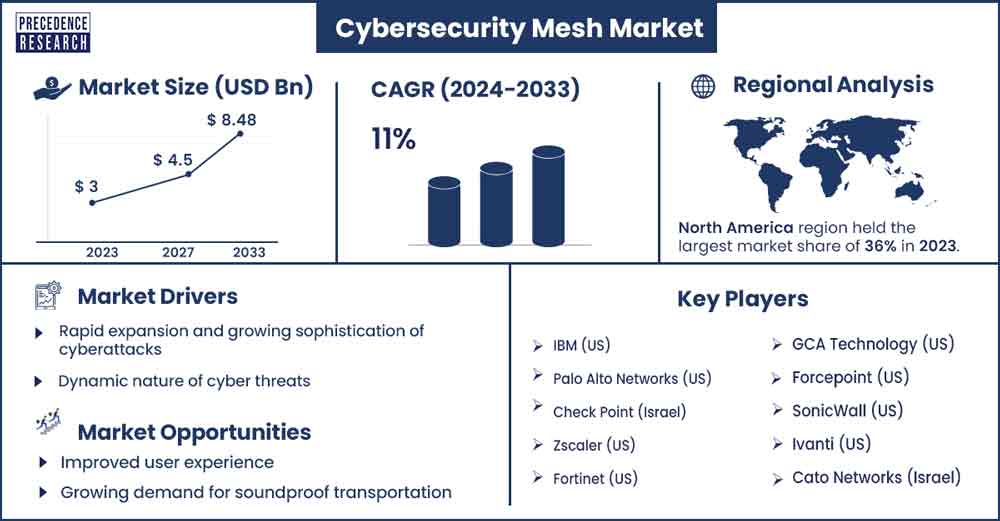
The global cybersecurity mesh market size was exhibited at USD 3 billion in 2023 and is anticipated to touch around USD 8.48 billion by 2033, expanding at a CAGR of 11% from 2024 to 2033.
Market Overview
The cybersecurity or cybersecurity mesh market offers solutions that improve detection capabilities, response times, consistency in policy administration, and adaptive access control while centralizing data and control. Principles of the Cybersecurity Mesh-
- A Zero Trust Architecture solution checks and authenticates, regardless of the network location or user/device identification.
- Instead of centralized security controls in one place, a decentralized method ensures they are dispersed throughout the network. This enables a security posture that is more resilient and adaptable.
- A feature known as interoperability promotes cooperation and communication between different security platforms and solutions, making it simple to share and integrate security data.
Regional Snapshot
North America's cybersecurity mesh market is expanding due to rising cyber threats, legal compliance, digital transformation, and cloud usage. Cybersecurity mesh solutions are being adopted by organizations to improve their security posture and defend against ever-changing threats. Growing cyber threats, legal compliance, digital transformation, and cloud adoption are some primary motivators. A decentralized method that meets the demands of these sectors and defends against cloud-based threats is provided by cybersecurity mesh.
Due to the EU's GDPR, rising cyber threats, digital transformation, and a strong emphasis on privacy and data protection, the cybersecurity mesh market in Europe is expanding. GDPR's stringent data protection regulations, the growth of phishing, ransomware, and insider threats, as well as the complexity of IT environments are driving forces in the industry. Because of the cybersecurity issues that industries like finance and healthcare face, cybersecurity mesh solutions have been adopted early to meet their specific security requirements.
Due to reasons including digital transformation, rising cyber risks, regulatory environment, cloud use, government initiatives, and increasing awareness, the cybersecurity mesh market in Asia-Pacific (APAC) is expanding rapidly. APAC countries use advanced security solutions such as cybersecurity mesh to defend against supply chain assaults, phishing, and ransomware. Organizations must strengthen their cybersecurity procedures due to the region's legal climate while adopting cloud computing, which offers scalability, flexibility, and cost-efficiency. Organizations are also encouraged to implement cutting-edge security measures through government efforts. The market is expanding due to rising awareness of cyber security dangers and the need for strong measures.
Cybersecurity Mesh Market Report Scope
| Report Coverage | Details |
| Market Revenue in 2023 | USD 3 Billion |
| Projected Forecast Revenue by 2032 | USD 8.48 Billion |
| Growth Rate from 2023 to 2032 | CAGR of 11% |
| Largest Market | North America |
| Base Year | 2022 |
| Forecast Period | 2023 to 2032 |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Market Dynamics
Drivers
Dynamic nature of cyber threats
Malicious actors employ continuously changing "cyber threats" strategies to take advantage of weaknesses and compromise data, networks, and digital systems. These dangers use cutting-edge methods, including automation, machine learning, and artificial intelligence. They can take many forms, including supply chain assaults, phishing, ransomware, and malware. Cyber risks change quickly due to technological advancements, security protocols, and detection tools. They focus on well-known hardware, software, configurations, and user behavior flaws, frequently taking advantage of them to gain unauthorized access or steal data. They can linger unnoticed, avoid discovery, and gradually exfiltrate data. Cyber risks are ubiquitous, affecting companies of all kinds and industries across the globe.
Demand for scalability and flexibility
Cloud computing, agile development, DevOps processes, varied workforces, fast growth, and change fuel the need for scalability and flexibility in cybersecurity solutions. Solutions that can handle growing digital footprints, varied workloads, and changing IT environments are required by organizations. Cloud-native security solutions must adjust to the flexibility and agility of cloud settings.
Adaptive security controls allow enterprises to uphold security and compliance standards while enforcing uniform policies in over-dispersed settings. DevOps methods and agile development approaches encourage speed, agility, and teamwork, and scalable and adaptable security solutions fit well with DevOps workflows. By utilizing technologies like artificial intelligence (AI), machine learning, behavioral analytics, and threat intelligence, adaptive security capabilities enable enterprises to reduce the impact of security breaches and stay ahead of new threats.
Restraints
Security risks
Complexity, interoperability problems, data privacy, and compliance, scalability issues, overlap or gaps in security controls, centralized points of failure, misconfiguration and human error, supply chain risks, and insider threats are just a few of the security risks that come with implementing a cybersecurity mesh. Configuration problems, misconfigurations, vulnerabilities, and unauthorized access to private information and systems can all result from these hazards. Because incompatible solutions might lead to defensive security gaps, security controls, and technology must work together. Scaling problems can lead to performance problems and more security breaches. Data privacy and compliance standards need to be carefully addressed. To reduce these risks, organizations must also implement strong configuration management and training programs.
High cost
The size, complexity, deployment area, technology employed, and customization of the organization all affect how much it will cost to put a cybersecurity mesh in place. Technology costs, integration costs, deployment costs, operating costs, training and awareness costs, professional services and consulting fees, possible non-compliance costs, and scaling costs are some of the significant expenses. Thereby, the cost associated acts as a restraint for the cybersecurity mesh market.
Acquisition and implementation of security controls are among the technology costs. The integration costs include custom development, testing, validation, and rollout. Maintenance and monitoring are among the operational costs. Employee and specialized training are among the training costs. External consultants are involved in consulting and professional services. Potential non-compliance costs include fines, legal fees, reputational harm, and business loss.
Opportunity
Improved user experience
The rising emphasis on improved user experience is observed to offer lucrative opportunities for the cybersecurity mesh market. Transparent security, consistent access, context-aware security, user education, expedited incident response, customized security policies, and feedback systems are just a few ways a cybersecurity mesh can improve user experience. Consistent access and authentication procedures simplify matters, while transparent security guarantees that users can carry out their activities without being bothered. Adaptive authentication and other context-aware security techniques enable easy resource access without compromising security. Programs for user education assist users in contributing to a secure environment and realizing the value of security. Users can recommend enhancements through feedback channels, enabling companies to modify their security protocols.
Recent Developments
- In January 2023, The BFSI sector, crucial for economic stability, is a significant cybercriminal target, undergoing a significant transformation in 2023 due to evolving threats and innovative countermeasures.
Key Market Players
- IBM (US)
- Palo Alto Networks (US)
- Check Point (Israel)
- Zscaler (US)
- Fortinet (US)
- GCA Technology (US)
- Forcepoint (US)
- SonicWall (US)
- Ivanti (US)
- Cato Networks (Israel)
- Aryaka Networks (US)
- SailPoint (US)
- appNovi (US)
- Appgate (US)
- Mesh Security (Israel)
- Primeter 81 (Israel)
- Naoris Protocol (Portugal)
- Exium (US)
Market Segmentation
By Offering
- Solutions
- Services
By Deployment
- Cloud
- On-premise
By Enterprise Size
- Small And Medium-Sized Enterprises (SMEs)
- Large enterprises
By Vertical
- BFSI
- Healthcare
- Energy Utilities
- IT and Telecom
- Government
- Others
Buy this Research Report@ https://www.precedenceresearch.com/checkout/3772
You can place an order or ask any questions, please feel free to contact at sales@precedenceresearch.com | +1 650 460 3308